Cyber crimes are criminal acts that are committed using the internet, computer networks, or other digital technologies. These crimes can range from relatively minor offenses, such as hacking into a social media account, to more serious crimes, such as identity theft, fraud, or cyber terrorism.
According to the latest data from the Australian Cyber Security Centre (ACSC), cybercrime continues to be a significant threat in Australia. In 2020, the ACSC received over 67,500 reports of cybercrime, representing an increase of 13% from the previous year.
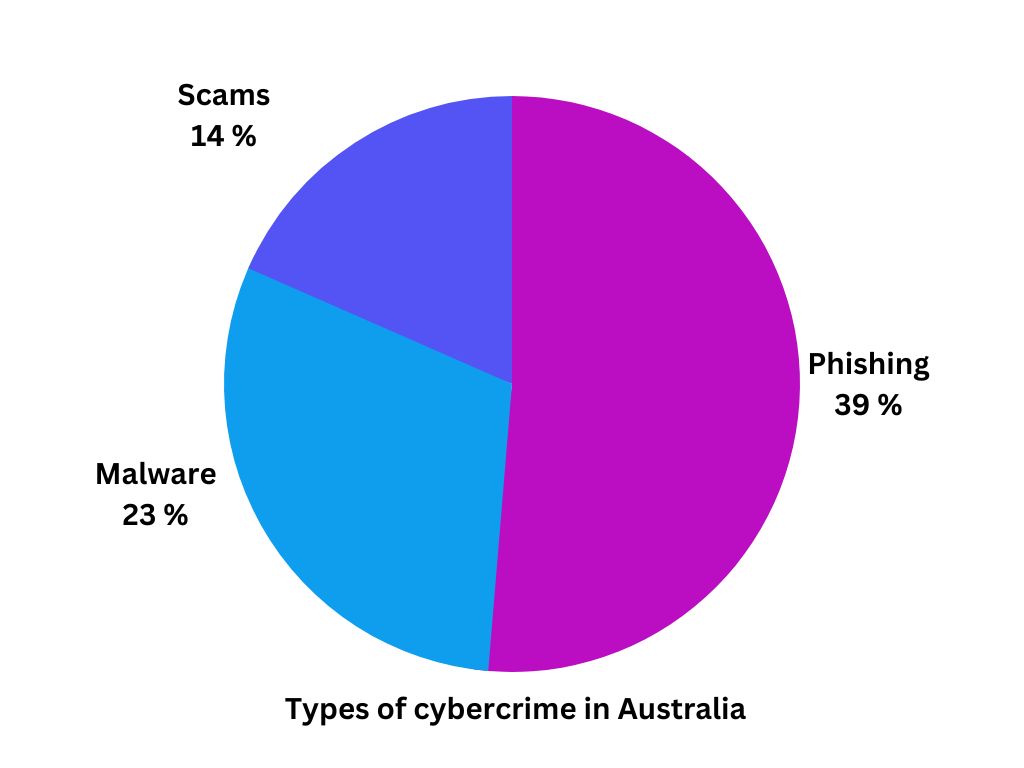
The most commonly reported types of cybercrime in Australia are phishing (39%), malware (23%), and scams (14%). And at this point, these attacks sometimes come in the form of a zero-day attack and keep on getting harder to defend from because they are targeting areas in software or hardware that have not been discovered or patched yet.
What is a Zero-Day Attack?
A zero-day attack is a type of cyber attack that exploits a software vulnerability that is unknown to the software vendor or the public. This vulnerability, also known as a zero-day vulnerability, is a flaw or weakness in a software program that can be exploited by attackers to gain unauthorized access to a system, steal data, or carry out other malicious activities.
The term "zero-day" refers to the fact that the vulnerability is unknown to the software vendor or security experts, meaning that there are no patches or updates available to fix the issue. This makes zero-day attacks particularly dangerous and difficult to defend against, as there may be no way to detect or prevent the attack until it has already occurred.
Zero-day attacks can be carried out in a variety of ways, including through phishing emails, malicious websites, or infected software downloads. They are often used by advanced persistent threat (APT) groups, nation-state actors, or other highly skilled attackers who are able to discover and exploit previously unknown vulnerabilities in software.
Examples of Zero-Day Attack
It's worth noting that zero-day attacks are relatively rare compared to other types of cyber attacks, as they require attackers to discover previously unknown vulnerabilities in software or hardware. But below are the list of reported zero-day attacks that happened recently:
In April 2023, according to an article released by SC Media, Google released an emergency update for Chrome to address a zero-day security flaw. This security flaw affects the desktop versions of the Google Chrome browser for Windows, macOS, and Linux that are older than build version 112.0.5615.121. “The vulnerability tracked as CVE-2023-2033 has a CVSS rating of high and is classified as a confusion flaw located in Chrome's V8 open-source JavaScript engine. NIST's description of the flaw describes the exploitation of the flaw allowing "a remote attacker to potentially exploit heap corruption via a crafted HTML page."
Cisco also disclosed in April that a zero-day vulnerability in the company's Prime Collaboration Deployment (PCD) software happened and that it can be exploited for cross-site scripting attacks. This utility for managing servers allows administrators to perform migration or upgrade tasks on servers listed in their organization's inventory. If successfully exploited, unauthenticated attackers can remotely launch cross-site scripting attacks; however, such attacks require user interaction.
In March 2023, Bitcoin ATMs owned by General Bytes were attacked by unidentified hackers who stole more than $1.6 million in cryptocurrency, according to an article released by Dark Reading. This incident from General Bytes was the second one in just under one year.
Source: https://www.zero-day.cz/
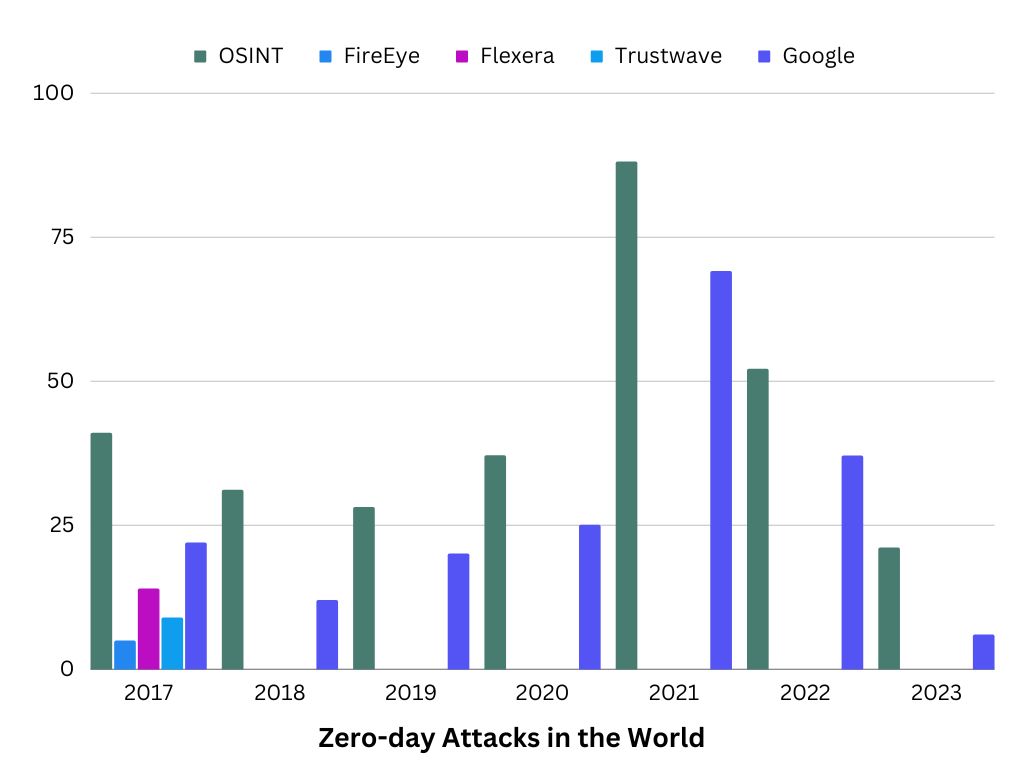
In the year 2021, it was reported that it has the highest record of zero-day hacking attacks which was twice as much from the previous year, according to multiple databases, researchers, and cybersecurity companies.
How Zero-Day Attack Affects Business
Zero-day attacks can cause serious damage to businesses of all sizes, as they can result in data breaches, financial losses, and reputational damage. To help you have a clear view of how much a certain attack can cost your company, here is a list of how zero-day attacks can affect businesses.
Data breaches
Zero-day attacks can be used to steal sensitive data, such as customer information, financial data, and intellectual property. This can lead to data breaches that can be costly and damaging to the affected business.
According to the 2022 Cost of a Data Breach Report by IBM, the average total cost of a data breach in Australia is AUD 4.36 million (approximately USD 2.92 million). This represents a significant increase from the previous year's report, which estimated the average cost of a data breach in Australia at AUD 4.21 million (approximately USD 2.82 million).
Financial losses
Zero-day attacks can also be used to carry out financial fraud, such as stealing funds from bank accounts or credit cards. Businesses can suffer significant financial losses as a result of these types of attacks.
Reputational damage
If a business suffers a data breach or other type of cyber attack, it can damage the company's reputation and erode customer trust. This can lead to lost business and reduced revenue over the long term.
Business disruption
Zero-day attacks can also disrupt business operations, as systems may need to be taken offline or reconfigured in order to address the vulnerability. This can result in lost productivity and revenue, as well as increased expenses associated with addressing the attack.
How To Detect Zero-Day Attack
Detecting a zero-day attack can be challenging, as these attacks exploit vulnerabilities that are not yet known or have not yet been patched. However, some techniques and strategies can help to detect and mitigate the risks of a zero-day attack.
Intrusion Detection Systems (IDS)
IDS can help to detect suspicious activity on a network by monitoring traffic and looking for patterns or behaviors that may indicate a potential attack. An IDS passively monitors network traffic or system logs for anomalous or suspicious activity, such as unauthorized access attempts or unusual data transfers. After monitoring, it correlates the events with known attack signatures or indicators of compromise (IOCs) to identify potential threats. If the IDS detects activity that matches a known attack signature or IOC, it generates an alert to notify security personnel or administrators of the potential threat. And lastly, based on the severity of the alert, security personnel may take a variety of actions, such as blocking traffic from a suspicious IP address or investigating a potential data breach.
Vulnerability scanning
Vulnerability scanning is an important component of a comprehensive cybersecurity program, as it helps to identify potential vulnerabilities before they can be exploited by attackers. However, it's important to note that vulnerability scanning is not a one-time process, as new vulnerabilities are discovered regularly. Regular scanning and patching are essential to maintaining a strong security posture and protecting against cyber attacks.
Endpoint protection
Endpoint protection software can help to detect and block malicious activity on individual devices, even in the case of a zero-day attack. It is designed to provide insight into endpoint activity, allowing you to automate responses to suspicious events and potentially prevent attacks from occurring, what’s better is that it is real-time.
User education and awareness
Educating employees about the risks of cyber attacks, including zero-day attacks, can help to increase awareness and reduce the likelihood of falling victim to these types of threats. To prevent these attacks, it's important to train employees to recognize and respond to suspicious activity within the network, applications, and services they use. Additionally, employees should be provided with a clear plan of action to follow in the event of a suspected compromise.
How To Be Safe From Zero-Day Attack
Zero-day attacks are exploits that take advantage of vulnerabilities in software or hardware that have not yet been discovered or patched. Enterprises or even small companies facing the dangers of zero-day attacks may feel hopeless, but the situation is not always as bleak as it seems.
Experts suggest that with the proper security guidance and adherence to cybersecurity best practices, it is possible to protect against zero-day attacks. Here are some of the best practices that your company can follow:
Get Help from Cybersecurity Experts
These experts don't mean you need to hire a whole team of cybersecurity professionals in-house because it would be costly. Partnering with a Managed Service Provider (MSP) is considered a great option for your cybersecurity needs especially if you’re on a tight budget.
Managed service providers (MSPs) can play a critical role in helping businesses improve their cybersecurity posture. They provide a full range of IT services including risk assessment, security monitoring, incident response, patch management, and employee training and they also ensure compliance with industry regulations and standards, such as HIPAA, PCI DSS, and GDPR to mention some.
By partnering with an MSP, businesses can benefit from their expertise and experience in managing and mitigating cyber risks.
Use Multiple Layers of Security
There are tools and other software that can be used to help prevent zero-day attacks. This includes the use of firewalls, antivirus, and antimalware software. A firewall can help prevent unauthorized access to your computer or network while antivirus and antimalware software can help detect and block known malicious software that may be used in zero-day attacks.
With the use of such software, your company might also want to consider keeping your software up-to-date. Software updates often include patches for known vulnerabilities. By keeping your software updated, you reduce the likelihood of falling victim to a known exploit.
Be Cautious of Email Attachments
Zero-day attacks often involve phishing emails that try to trick users into downloading malicious software or visiting compromised websites. Be cautious of emails from unknown senders, especially if they contain attachments or links.
Educate Employees
Educating employees about the risks of cyber attacks, including zero-day attacks, can help to raise awareness and reduce the likelihood of a successful attack. Stay informed about the latest security threats and best practices for staying safe online.
Final Thoughts
Overall, preventing zero-day attacks requires a comprehensive and proactive approach to cybersecurity, including regular updates, employee education, and effective monitoring and response capabilities. By staying informed about the latest threats and best practices, organizations can better protect themselves against the risks of zero-day attacks and other types of cyber threats.
Ready to get help from an expert for your cybersecurity needs? Contact us today!

Leave a comment!