MDR vs EDR: Understanding What Each One Does

When evaluating cybersecurity solutions, many business leaders encounter the comparison of MDR vs EDR. They are often positioned as alternatives, which creates unnecessary confusion. In reality, they serve different purposes and address different challenges within an organisation’s security strategy.
Rather than asking which one is better, it is more useful to understand what each one is designed to do, where it fits, and why comparing them directly can be misleading.
This article explains what EDR and MDR are, how they are used, their benefits, and why MDR vs EDR should not be treated as a competitive decision.
What is EDR and what is it used for?
EDR, or Endpoint Detection and Response, is a cybersecurity technology that monitors activity on endpoints such as laptops, desktops, servers, and virtual machines.
Endpoints are a primary target for attackers, which makes visibility at this level critical. EDR provides visibility by continuously collecting data and analysing behaviour on each device.
How EDR works in practice
EDR focuses on detecting suspicious behaviour rather than relying solely on known malware signatures. This allows it to identify modern threats such as ransomware activity, credential misuse, malicious scripts, and unauthorised privilege escalation.
When suspicious behaviour is detected, EDR generates alerts and provides detailed context so IT or security teams can investigate what happened, how it started, and whether it spread.
Most EDR platforms also include response capabilities, such as isolating a device or terminating a malicious process. However, these actions still rely on someone making the right decision at the right time.
Benefits of EDR
EDR strengthens security posture by improving visibility across endpoints and enabling faster investigation of incidents. It supports compliance and audit requirements through detailed logs and forensic data, and it detects threats that traditional antivirus solutions often miss.
For organisations with in-house security capability, EDR is an important foundational control.
The limitation of EDR
EDR is a tool, not a security team. Alerts must be monitored, analysed, and acted on. If alerts are missed, misunderstood, or delayed, the technology alone cannot prevent a breach from escalating.
This operational gap is where many organisations struggle.
What is MDR and what is it used for?
MDR, or Managed Detection and Response, is a managed security service that combines detection technology with continuous monitoring, investigation, and response by security professionals.
MDR exists to solve a practical problem. Many organisations deploy strong security tools but do not have the resources or specialist skills to operate them effectively 24/7.
How MDR works
MDR providers actively monitor environments around the clock. When alerts occur, they investigate activity to determine whether it represents a genuine threat or a false positive.
If a threat is confirmed, MDR teams take immediate action to contain it. This may include isolating devices, disabling compromised accounts, or stopping malicious processes. Incidents are documented and reported clearly, so businesses understand what happened and how it was handled.
Benefits of MDR
MDR reduces risk by significantly shortening response times. This is critical for ransomware and data breach scenarios, where minutes can make a material difference.
It also removes the burden from internal IT teams, allowing them to focus on operational priorities while security monitoring and response are handled by specialists. MDR provides accountability, consistency, and confidence that threats are being actively managed.
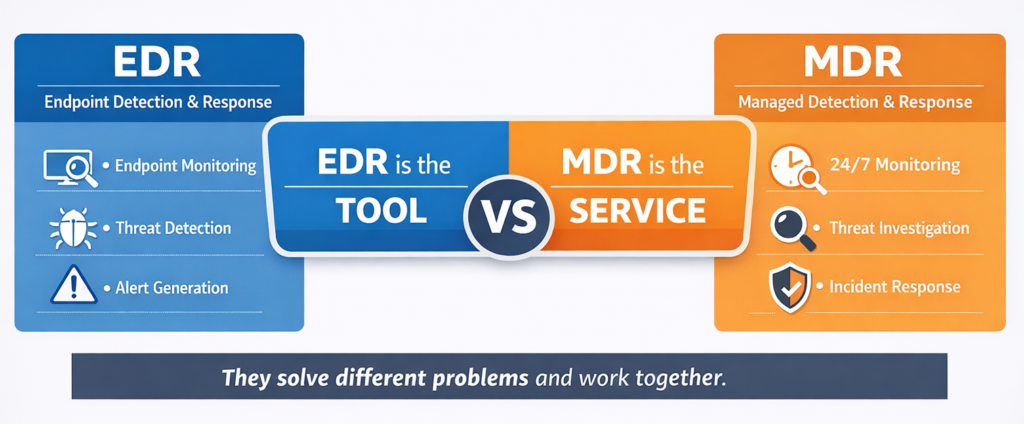
MDR vs EDR: key differences in responsibility
The MDR vs EDR discussion often focuses on features, but the real difference is responsibility.
EDR provides detection and insight. The organisation remains responsible for monitoring alerts, investigating incidents, and responding appropriately.
MDR assumes responsibility for detection and response. Security professionals monitor alerts continuously, investigate incidents, and take action on behalf of the organisation.
In practical terms, EDR tells you something may be wrong. MDR determines whether it is wrong and resolves it.
Common misunderstandings about MDR vs EDR
One common misconception is that MDR is simply an upgraded version of EDR. In reality, MDR relies on EDR or similar technologies, but its value lies in the service layer, people, processes, and accountability.
Another assumption is that deploying EDR alone is sufficient. Many organisations discover after an incident that alerts were missed, delayed, or misinterpreted, particularly outside business hours.
Why MDR vs EDR should not be compared
This is the key takeaway.
MDR vs EDR should not be treated as a comparison between two competing solutions.
EDR answers the question, “What is happening on our endpoints?”
MDR answers the question, “Who is watching, and who is responding when it matters?”
They address different needs. Understanding what each one is used for allows businesses to make informed decisions about capability, risk tolerance, and operational responsibility.
For most organisations, the real decision is not MDR vs EDR. It is whether they want to manage detection and response internally or rely on a managed service designed to do that job continuously.
How Affinity MSP approaches MDR and EDR
At Affinity MSP, we focus on security outcomes rather than individual tools. EDR is an essential component of modern cybersecurity, but tools alone do not stop incidents.
Our approach combines EDR technology with managed detection, response, and clear communication. Clients are not left interpreting alerts or making critical decisions under pressure. Threats are monitored, investigated, and addressed with accountability and transparency.
To see how MDR and EDR fit into a broader cybersecurity approach, you can explore our Cybersecurity Services offering on our website.